As a client, the application makes requests to display or act on some content. The application can register a listener with Registry. The veracity of the ID can be cross checked with the authority information that provided for content handlers and invoking applications. Leading and trailing whitespace is deleted. Authentication of applications and application classes MUST conform to the requirements of the applicable Java runtime environment. Version numbers are formatted so they can be used by the application management software for install and upgrade uses, as well as communication with the user. 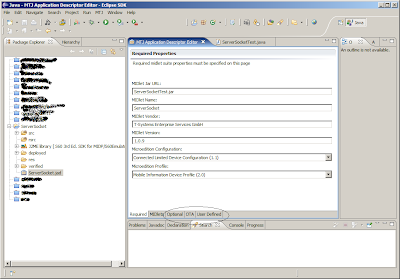
| Uploader: | Faek |
| Date Added: | 26 October 2011 |
| File Size: | 17.43 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 48628 |
| Price: | Free* [*Free Regsitration Required] |
In addition, each portion of the version number is allowed a maximum of two decimal digits i. The implementation MUST ensure that the application programmer cannot override, modify, or add any classes to these protected system packages.
Any additional entries are ignored. Each Java runtime specifies how applications are uniquely identified, for example, by a classname of the application class. If a device supports multiple VMs, each may have its own jxvax, naming, and resource management policies.
java - where can i find the jar? - Stack Overflow
The JAR manifest defines attributes that are used by the application management software to identify and install the MIDlet suite and as defaults for attributes not found in the application descriptor. This state is entered: The following attributes can be included in the JAR manifest of the application. The application management software creates a new instance of a MIDlet.
If there is a conflict between foreground transitions and external events or explicit user actions, then the external events or user actions should take precedence. Installation and removal of content handlers utilizes the normal mechanisms of the Java runtime environment. The content handler can register a listener with ContentHandlerServer. Name is used to identify this MIDlet to the user. Copyright Sun Microsystems, Inc.
The predefined attributes listed below allow the application management software to identify, retrieve, install, and invoke the MIDlet.
These files are containing the class javax.microedition
Jat MIDlet state machine is designed to ensure that the behavior of an application is consistent and as close as possible to what device manufactures and users expect, specifically:. The bold text indicates additions to support content handlers.
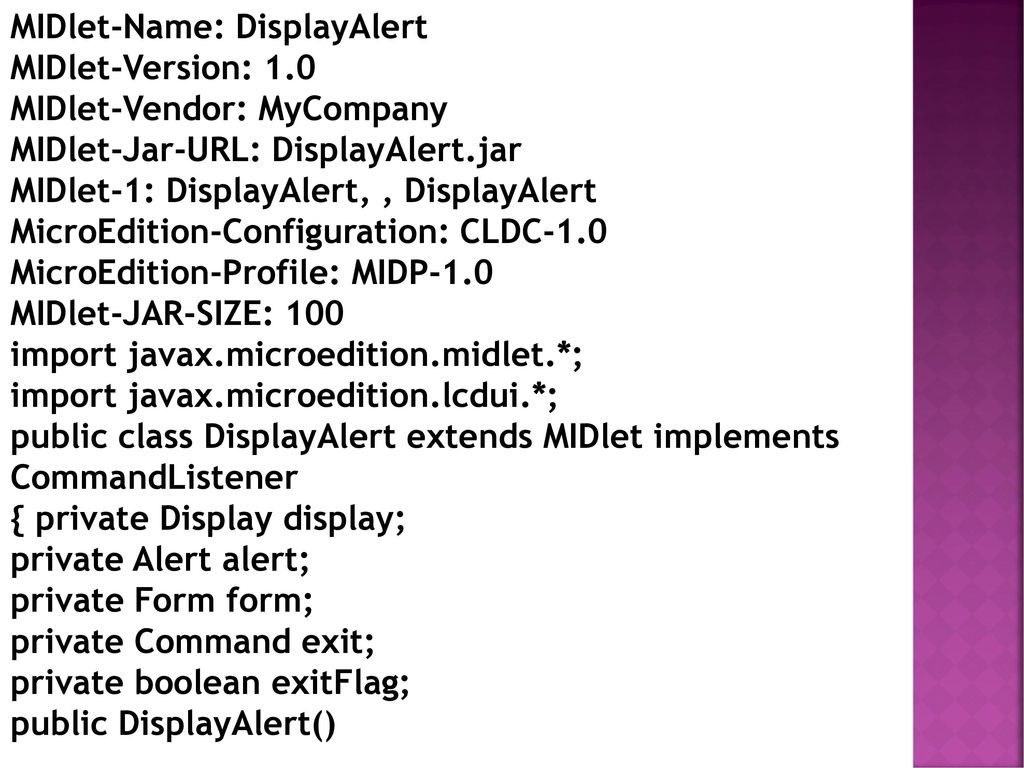
A JAD file is a text file that you can create with any text editor. If the number of action names does not match the number of actions, then the installation MUST fail. The installation notifications are: The device must implement all of the profiles listed. ContentHandlerServer provides methods to get new Invocation requests, to finish the processing of requests and to get the access control information. The authority for a signed MIDlet suite is the value of the Subject field of the signing certificate.
Download midp_2.1.jar : midp « m « Jar File Download
This state is entered:. If the application needs to know when a request is complete or to get a result it can require a response from the content handler.
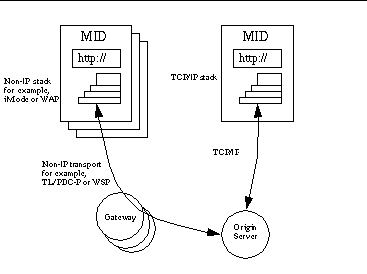
The content handler uses the parameters in the Invocation to process the request. ContentHandler permission to perform either static or dynamic registrations consistent with the device's security policy.
The application calls the Registry. Invocation An Invocation contains the parameters that are passed from an invoking application to a content handler and the results that are returned to the application. The organization that provides the MIDlet suite.
The MIDlet has released all of its resources and terminated.
MID Profile: Package
The contents of the MIDlet descriptor file, when it is present, are made javxa via the javax. For example, an ISO encoded file would need to be read through the equivalent of java.
If there are any dynamic registrations, then they MUST be retained across the upgrade unless superceded by a new static registration for the same classname. The content handler uses the URL, type, and action to determine how it should act on the content. Security for MIDP Applications section describes the concepts and capabilities of untrusted and trusted applications.

No comments:
Post a Comment